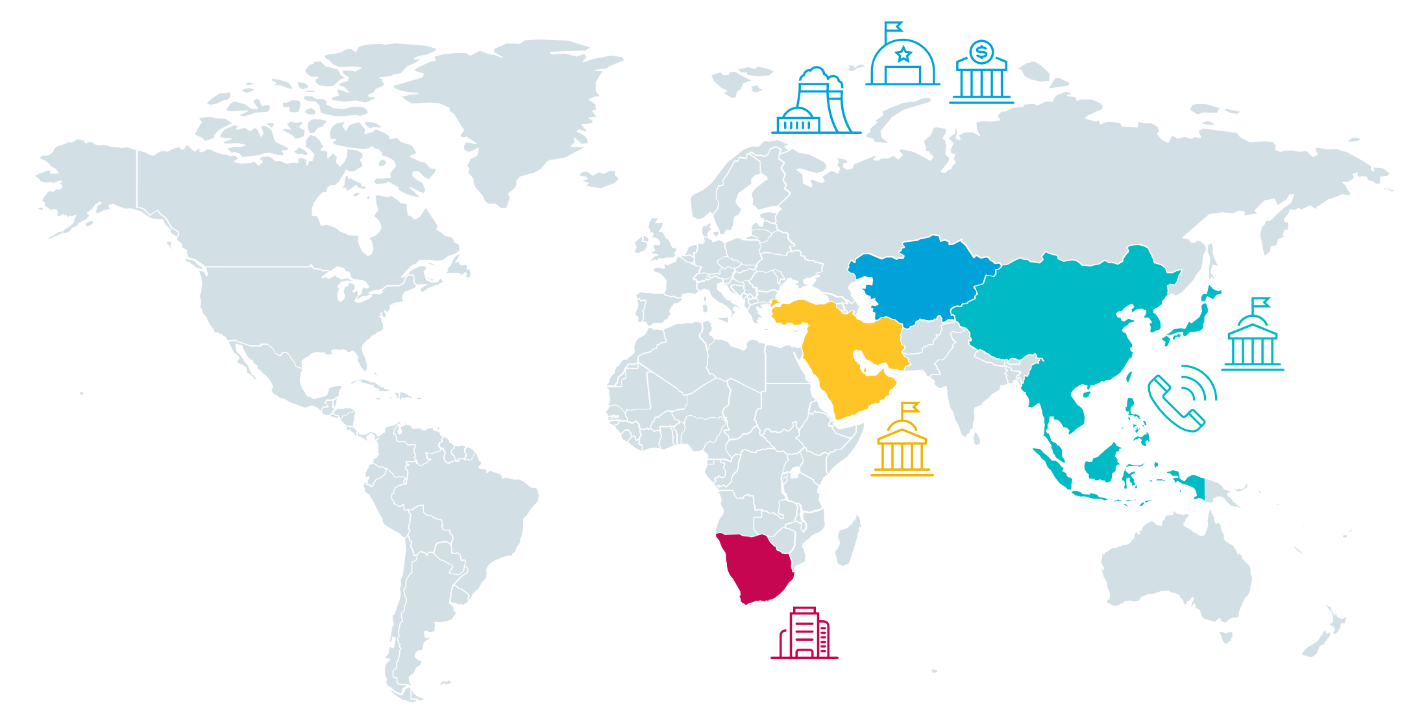
Several high-profile organizations in the telecommunications, banking, maritime, energy, military, government and public sectors are under attack. The targets are mainly located in Asia, but also in the Middle East and Africa
ESET researchers recently discovered targeted attacks that used undocumented tools against various high-profile companies and local governments mainly in Asia, but also in the Middle East and Africa.
These attacks were conducted by a previously unknown cyber espionage group which ESET has named Worok. According to ESET's telemetry, Worok has been active since at least 2020 and continues to be active today. Targets include companies in the telecommunications, banking, maritime, energy, military, government and public sectors. In some cases, Worok used the notorious ProxyShell vulnerabilities to gain initial access.
"We believe malware operators are on the hunt for information because they focus on high-profile entities in Asia and Africa, targeting various sectors, both private and public, but with a specific emphasis on government organizations," he says Thibaut Passilly, ricercatore ESET who discovered Worok.
At the end of 2020, Worok targeted entities and companies in several countries, most notably: a telecommunications company in East Asia; a banking institution in Central Asia; a company in the maritime sector in Southeast Asia; a government agency in the Middle East; a private company in South Africa.
There was a significant disruption of operations observed from May 2021 to January 2022, but Worok's business resumed in February 2022, against an energy company in Central Asia and a public sector entity in Southeast Asia. .
Worok is a cyber espionage group that develops its own tools and exploits existing ones to compromise its objectives. The group's custom toolset includes two loaders, CLRLoad and PNGLoad, and a backdoor, PowHeartBeat.
CLRLoad is a tier one loader used in 2021, but replaced in 2022, in most cases, by PowHeartBeat. PNGLoad is a second level loader that uses steganography to reconstruct malicious payloads hidden in PNG images.
PowHeartBeat is a complete backdoor written in PowerShell, obfuscated using various techniques such as compression, encryption and encryption. This backdoor has various capabilities, including executing commands / processes and manipulating files. For example, it is able to upload and download files from compromised machines; to return information about the files to the command and control server such as the path, length, creation time, access times and content; to delete, rename and move files.
“Although our knowledge at this stage is limited, we hope that putting the spotlight on this group will encourage other researchers to share information about it,” Passilly adds.
For more technical information on Worok, check out the blogpost Worok: the big picture su WeLiveSecurity.






