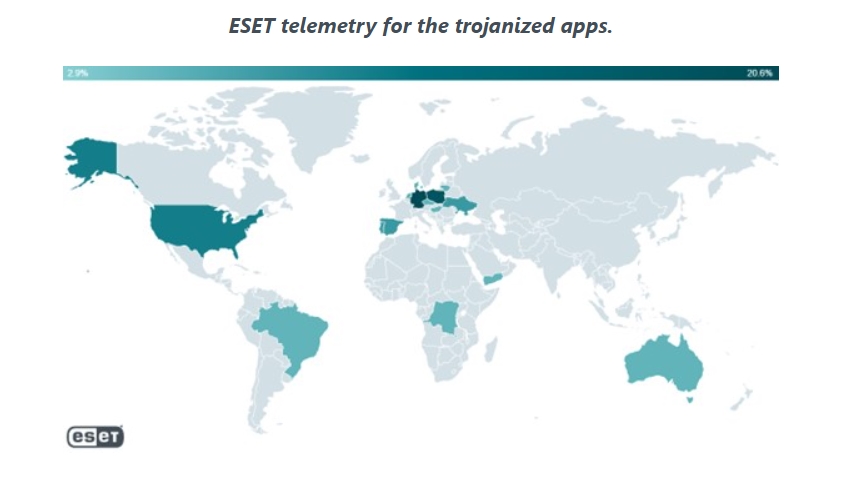
Thousands of users have downloaded the FlyGram and Signal Plus Messenger spy apps from the Google Play Store and Samsung Galaxy Store. ESET telemetry has reported detections on Android devices in Europe, the US, Ukraine and other parts of the world
Researchers of ESET, a global European leader in the cybersecurity market, have identified two active campaigns targeting Android users of Telegram and Signal, where the threat actors are traced back to the China-aligned APT GREF group. Most likely active since July 2020 and July 2022, for each app respectively, the campaigns distributed the BadBazaar Android spy code through the Google Play Store, Samsung Galaxy Store, and dedicated websites posing as legitimate encrypted chat applications – the malicious apps are FlyGram and Signal Plus Messenger. Threat actors gained the functionality of fake Signal and Telegram apps by patching the open-source Signal and Telegram apps for Android with malicious code. Signal Plus Messenger is the first documented case of spying on a victim's Signal communications; thousands of users have downloaded spy apps. ESET telemetry has reported detections on Android devices in several countries in the European Union, the United States, Ukraine and other countries around the world. Both apps were later removed from Google Play.
“BadBazaar's malicious code was hidden in Trojan-affected Signal and Telegram apps, which provide victims with a working app experience, but with spying activity in the background,” he explains Lukáš Štefanko, ESET researcher who made the discovery. “The main purpose of BadBazaar is to exfiltrate your device information, contact list, call logs and installed apps list, and to conduct spying on Signal messages by secretly connecting the Signal Plus Messenger app of the victim to the attacker's device,” he adds.
ESET telemetry reports detections from Australia, Brazil, Denmark, Democratic Republic of Congo, Germany, Hong Kong, Hungary, Lithuania, Netherlands, Poland, Portugal, Singapore, Spain, Ukraine, United States and Yemen. Additionally, a link to FlyGram in the Google Play Store was also shared in a Uyghur Telegram group. BadBazaar malware applications have previously been used against Uyghurs and other Turkic ethnic minorities outside of China.
As a partner of the Google App Defense Alliance, ESET identified the latest version of Signal Plus Messenger as malicious and promptly shared its findings with Google. Following the report, the app was removed from the Store. Both apps were created by the same developer and share the same malicious features, and the app descriptions on both stores reference the same developer's website.
After the initial start of the app, the user must access Signal Plus Messenger through the legitimate functionality of Signal, just as it would do with the official app for Android. Once the access has been made, Signal Plus Messenger begins to communicate with its Command and Control server (C&C). Signal Plus Messenger can spy on the messages of Signal abusing the "connecting device" function. It does so by automatically connecting the device compromised to the agrees' signal device. This spying method is unique: ESET researchers have never found a similar functionality used improperly by other malware and this is the only method with which the attacker can access the content of Signal's messages. ESET Research informed the Signal developers of this flaw.
As for the false telegram app, Flygram, the victim must access through the legitimate functionality of Telegram, as requested by the official app. Before the login is completed, Flygram begins to communicate with the C&C and Badbazaar server obtains the opportunity to exfiltrate sensitive information from the device. Flygram can access Telegram backups if the user has activated a specific function added by the attackers, a function that has been activated by at least 13,953 user account. The attacker's proxy server can be able to record some metadata, but cannot decrypt the data and messages actually exchanged within Telegram. Unlike Signal Plus Messenger, Flygram does not have the ability to connect a Telegram account to the attacker or to intercept the encrypted communications of his victims.
For more technical information on GREF's latest campaigns regarding BadBazaar and trojan-infected spy apps, please see the blog post “BadBazaar espionage tool targets Android via trojanized Signal and Telegram apps” su WeLiveSecurity.






