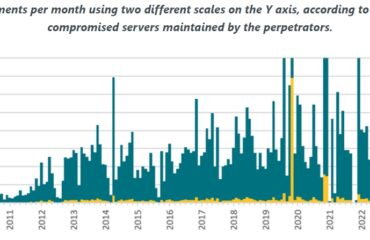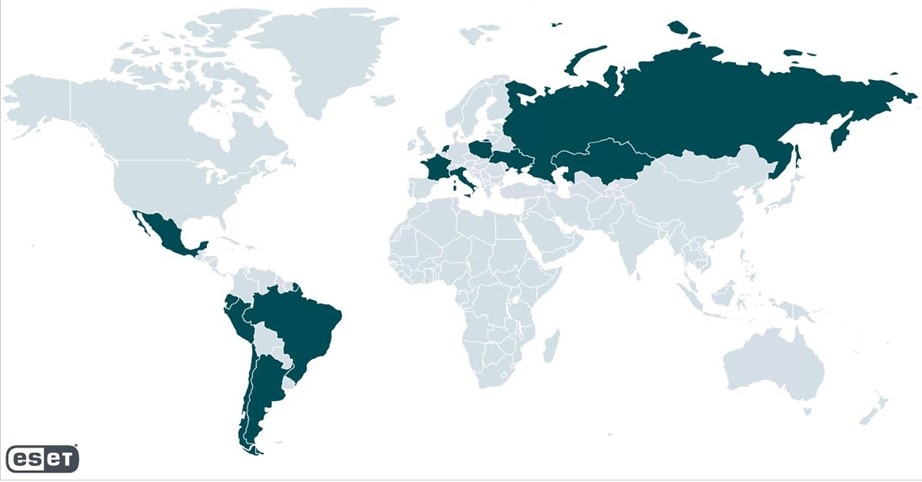
The operation, which dates back to at least April 2023, is still ongoing. Targets include SMEs and government entities with the majority located in Poland; other European and Latin American countries were also affected
Researchers of ESET, a global European leader in the cybersecurity market, have uncovered a large-scale phishing campaign aimed at harvesting the credentials of users of Zimbra email accounts. The operation has been active since at least April 2023 and is still ongoing. Zimbra Collaboration is an open-core collaborative software platform, a popular alternative to enterprise email solutions. The campaign targets small and medium-sized businesses and government entities. According to ESET telemetry, the largest number of lenses is located in Poland; however, companies in other European countries including Ukraine, Italy, France and the Netherlands were also targeted. Latin American countries have also been affected, with Ecuador at the forefront.
While the operation is not particularly technically sophisticated, it is still capable of spreading and successfully compromising organizations using Zimbra Collaboration. “Hackers exploit the fact that HTML attachments contain legitimate code, with the only telltale element being a link pointing to the malicious host. In this way, it is much easier to circumvent reputation-related anti-spam policies, especially compared to more popular phishing techniques, in which a corrupted link is inserted directly into the body of the email,” explains Viktor Šperka, ESET researcher who discovered the countryside.
“The target organizations are of various types; the attackers do not focus on any specific vertical: the only aspect that connects the victims is the use of Zimbra,” adds Šperka. Zimbra Collaboration's popularity among organizations with smaller IT budgets makes it an attractive target for adversaries.
Initially, the victim receives an email with a phishing page in the attached HTML file. The message alerts you to an email server update, account deactivation, or similar issue and prompts you to click on the attached file. After opening the attachment, the user is presented with a fake Zimbra login page customized to the target organization. In the background, the submitted credentials are collected by the HTML form and sent to a server controlled by the attacker. Then, the attacker is potentially able to infiltrate the hacked email account. It is likely that the malicious operators managed to compromise the administrator accounts of the victims and created new email inboxes which were then used to send phishing emails to other targets. The campaign observed by ESET is based only on social engineering and user interaction; however, this may not be the only case.