The report summarizing the activities of the APT groups in Q4 2022 and Q1 2023 has been published
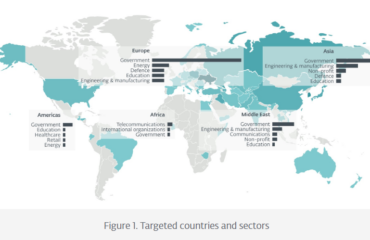
Milan, 10 May 2023 – ESET, a global European leader in the cybersecurity market, has published l’ESET APT Activity Reportwhich provides an analysis of ESET's research on the activities of Advanced Persistent Threat Groups (APTs), covering the period October 2022 – March 2023. The Report is released on a semi-annual basis. During this time, several China-affiliated groups, such as e3chang and Mustang Panda, focused on European organizations. In Israel, Iran-aligned group OilRig has implemented a new custom backdoor. Groups pro-North Korea continued to focus on South Korean and South Korean-related subjects. Pro-Russian APT groups were particularly active in Ukraine and European Union countries, with Sandworm distributing wipers.
The activities described in the report are detected by ESET technology. “ESET products protect our customers' systems from the malicious activity described in this report. The shared information is mainly based on ESET's proprietary telemetry data and has been verified by ESET researchers,” he explains Jean-Ian Boutin, Direttore di ESET Threat Research.
China-affiliated Ke3chang resorted to distributing a new variant of Ketrican, while Mustang Panda used two new backdoors. MirrorFace targeted Japan and implemented new malware distribution approaches, while Operation ChattyGoblin compromised a gambling company in the Philippines by targeting its support workers. The India-aligned SideWinder and Donot Team continued to target government institutions in South Asia: the former targeted the education sector in China, while the latter continued to develop the infamous yty framework, but also implemented the commercially available Remcos RAT. Also in South Asia, ESET Research has detected a high number of Zimbra webmail phishing attempts.
In addition to targeting employees of a defense contractor in Poland with a bogus Boeing-themed job offer, the Lazarus Group, near North Korea, has also shifted its focus from its usual vertical targets to a data management in India, using an Accenture themed lure. ESET has also identified a component of Linux malware exploited in one of their campaigns. The similarities to this newly discovered malware support the notion that the group is responsible for the attack on the 3CX supply chain.
Russian-aligned APT groups have been particularly active in Ukraine and EU countries, with Sandworm deploying wipers (including a new one that ESET calls SwiftSlicer) and Gamaredon, Sednit and Dukes using spearphishing emails that , in the case of Dukes, led to the execution of a red team rig known as Brute Ratel. Finally, ESET found that the aforementioned Zimbra email platform was also being exploited by Winter Vivern, a group particularly active in Europe, and researchers noticed a significant drop in the activity of SturgeonPhisher, a group that targets government of Central Asian countries with spearphishing emails, suggesting that the group is currently reorganizing.
For more technical information, consult the full version of theESET APT Activity Report su WeLiveSecurity.
ESET APT Activity Reports contain only a fraction of the cybersecurity intelligence data provided to customers. ESET produces in-depth technical reports and frequent updates on the activities of specific APT groups in the form of ESET APT Reports PREMIUM to help organizations charged with protecting citizens, critical national infrastructure and high-value assets from criminal and nation-state-directed cyber-attacks. More information on ESET APT Reports PREMIUM, which provides high-quality information on strategic and tactical cybersecurity threats, can be found at ESET Threat Intelligence.