Spacecolon distributes variants of the Scarab ransomware, which ESET believes is of Turkish origin. The largest detections in European countries, including Italy, in Türkiye and Mexico. Spacecolon acts as a remote access trojan with the ability to extract sensitive data and/or distribute the Scarab ransomware
ESET, a global European leader in the cybersecurity market, has published analysis of Spacecolon, a small toolset used to deploy variants of the Scarab ransomware around the world. The tool likely penetrates organizations through operators compromising vulnerable web servers or RDP credentials through brute forcing. Several versions of Spacecolon contain code sequences compiled in Turkish that ESET believes to be the work of a Turkish-speaking developer. ESET has managed to trace the origins of Spacecolon from May 2020 to the present. To represent the connection with “space” and the “beetle”, ESET gave Spacecolon operators the name CosmicBeetle.
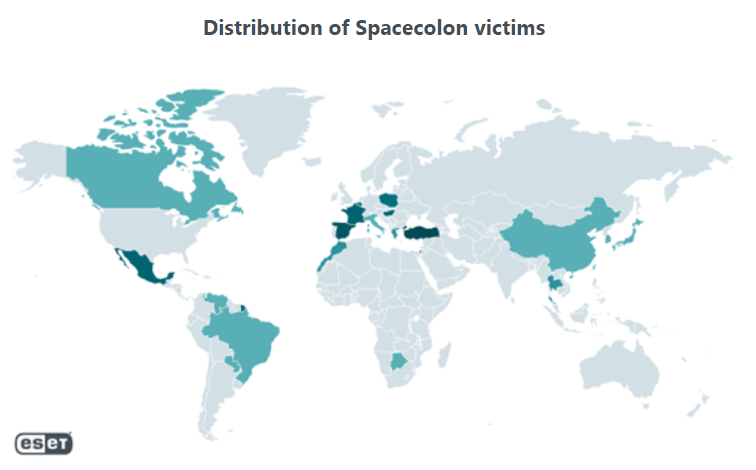
Spacecolon incidents identified by ESET telemetry are widespread across the world, with a high prevalence in European Union countries, such as Italy, Spain, France, Belgium, Poland and Hungary; Furthermore, ESET has detected a high prevalence in Türkiye and Mexico. CosmicBeetle appears to be preparing the distribution of a new ransomware, ScRansom. After the compromise, in addition to installing the ransomware, Spacecolon offers a large variety of third-party tools that allow attackers to disable security products, extract sensitive information, and gain further access.
“We did not observe any default pattern by which Spacecolon chose its victims, other than their vulnerability to the initial access methods used by CosmicBeetle. Nor did we find any correlation with focus areas or goal sizes. However, to name a few examples (by type and geography), we observed Spacecolon in a hospital and tourist resort in Thailand, in an insurance company in Israel, in a local government institution in Poland, in an area entertainment operator in Brazil, in an environmental services company in Turkey and in a school in Mexico,” he explains Jakub Souček, ESET researcher and author of the analysis.
CosmicBeetle likely compromises web servers exposed to the ZeroLogon vulnerability or those with RDP credentials that it is able to crack. Additionally, Spacecolon can provide backdoor access to its operators. CosmicBeetle makes no effort to hide malware and leaves numerous artifacts on compromised systems.
After compromising a web server, CosmicBeetle distributes ScHackTool, the main component of Spacecolon used by CosmicBeetle. It relies heavily on the graphical interface and the active participation of its operators; allows them to orchestrate the attack, downloading and running additional tools on the compromised machine on demand, as they see fit. If the target is deemed valuable, CosmicBeetle can deploy ScInstaller and use it, for example, to install ScService, which provides additional remote access.
The latest payload deployed by CosmicBeetle is a variant of the Scarab ransomware that internally implements a ClipBanker, a type of malware that monitors the contents of the clipboard and changes what it believes may be a cryptocurrency wallet address to an address controlled by the attacker.
Additionally, a new family of ransomware is under development, samples of which were uploaded to VirusTotal from Turkey. ESET Research called it ScRansom and believes, with extreme certainty, that it was written by the same developers as Spacecolon. ScRansom attempts to encrypt all hard, removable and remote drives. ESET has not yet observed this ransomware in action as it appears to still be in development.
For more technical information on Spacecolon and CosmicBeetle, check out the blog post “Scarabs colon-izing vulnerable servers” su WeLiveSecurity.